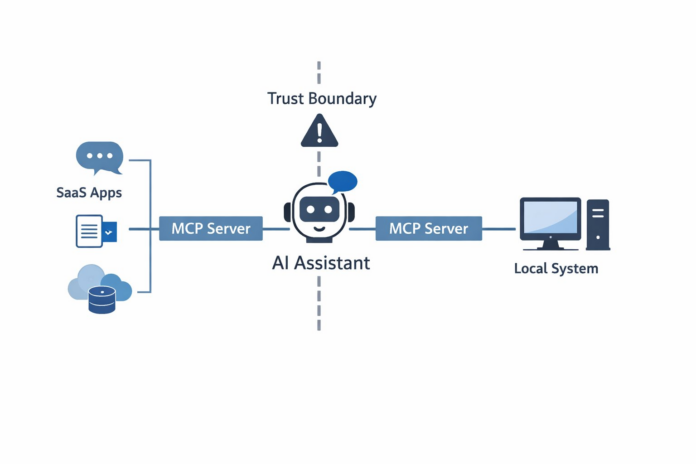
As enterprises rapidly adopt AI assistants, a new security concern arises with Model Context Protocol (MCP) servers, which connect AI applications to external tools. Vulnerabilities in MCP servers can be exploited for code execution, data exfiltration, and social engineering attacks, often without user awareness. The open-source MCP standard facilitates AI interactions but poses inherent risks by integrating into sensitive enterprise systems. Local MCP servers may execute code with the user’s privileges, while remote servers can access enterprise data and initiate OAuth flows, potentially leading to serious breaches when combined maliciously. Attackers can chain MCP servers, using trusted data sources as command-delivery channels, resulting in unnoticed data exfiltration. Protecting against these risks requires a comprehensive strategy that includes governance, restricted permissions, robust logging, and supply chain defenses. Organizations should treat MCP configurations as critical infrastructure, implementing zero-trust principles to bolster security in AI-driven environments.
Source link
Share
Read more