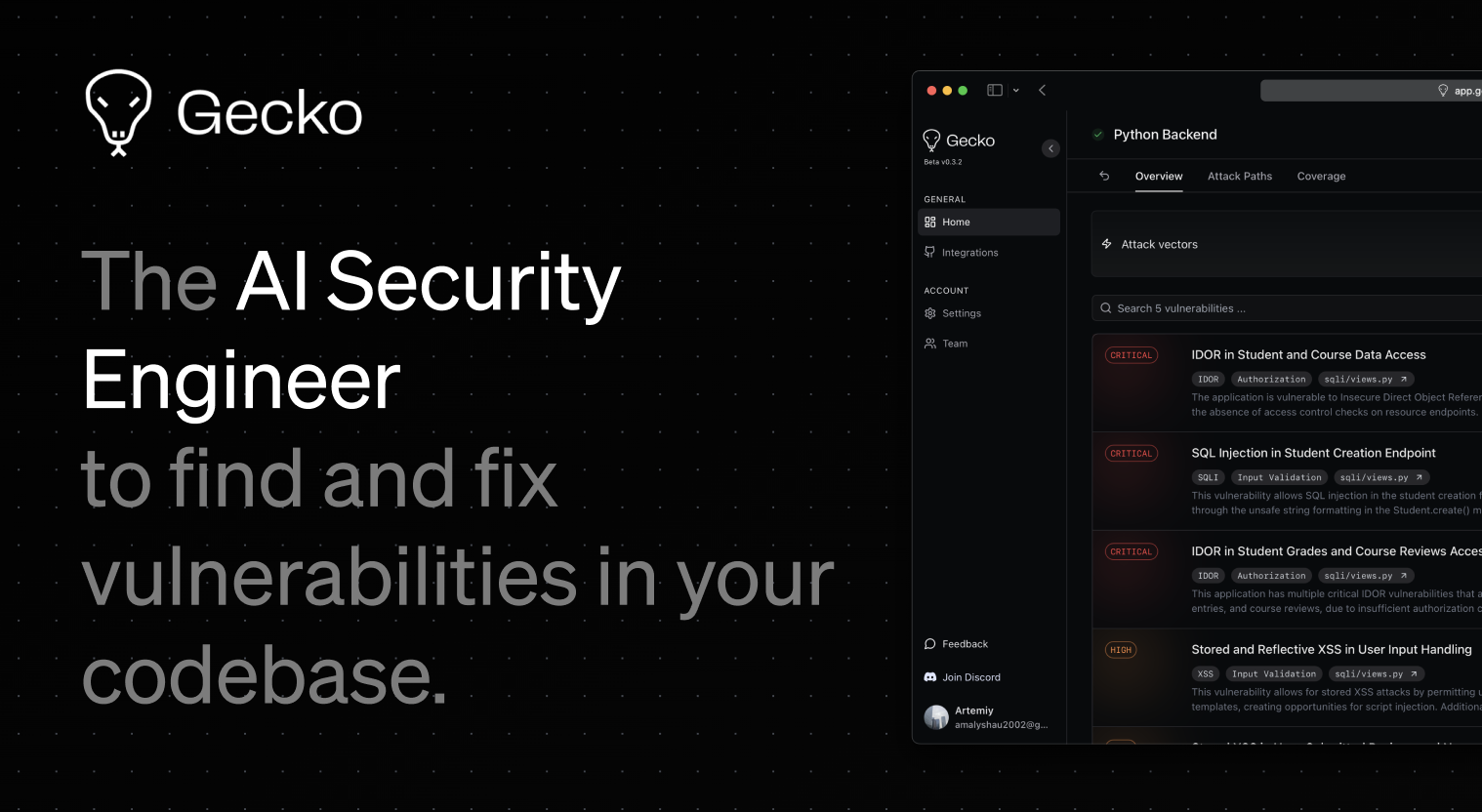
Unlocking Security: How AI is Revolutionizing Vulnerability Detection
Cal.com, an open-source scheduling solution, recently faced critical security vulnerabilities, allowing attackers to take over user accounts. With the help of Gecko’s AI-driven static analysis, these complex chained vulnerabilities were uncovered quickly—demonstrating the power of modern security tools.
Key Highlights:
- Vulnerability Discovery: Gecko autonomously identified issues within hours that traditional methods missed.
- Impact: Complete account takeovers and exposure of sensitive booking data were reported.
- AI-Augmented Security: Gecko’s unique approach revolutionizes how developers can secure their applications, making vulnerability detection as accessible as writing code.
Why It Matters:
- Democratizing Security: Gecko aims to empower every developer with robust tools to safeguard their applications.
- Proactive Defense: Understanding that layered security is vital, the findings emphasize the need for constant vigilance against potential threats.
Join the conversation and explore how AI can transform your software security practices. 💡 Share your thoughts below!