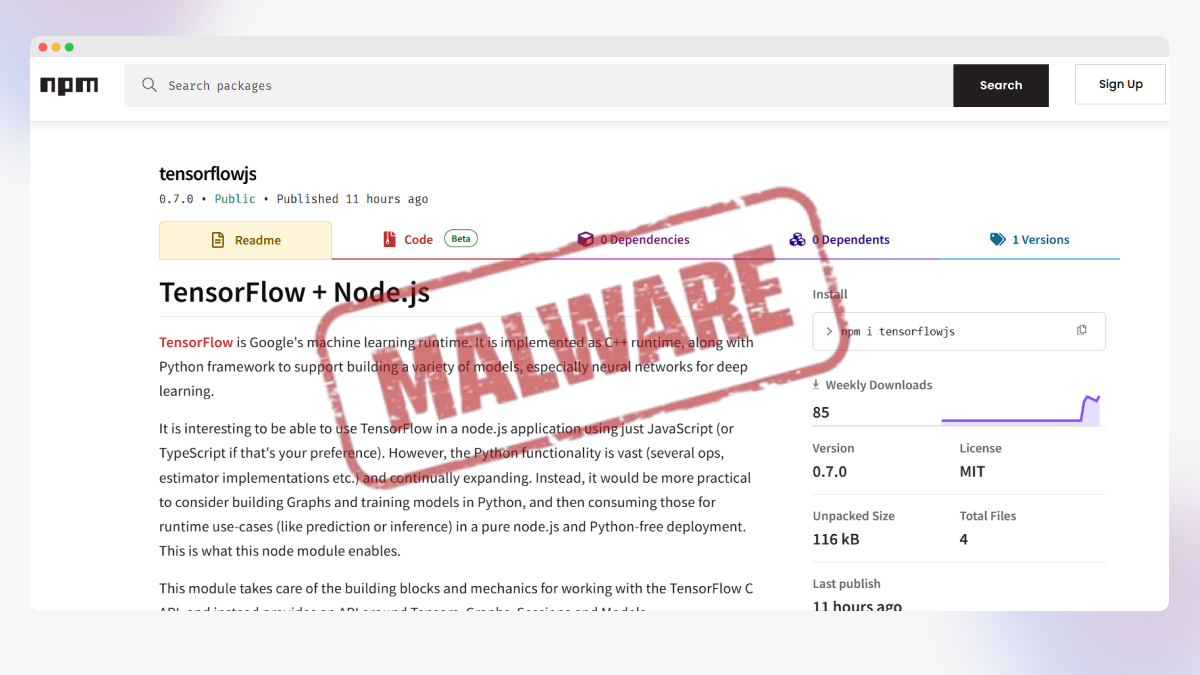
🚨 Alert for TensorFlow.js Developers: Sophisticated Typosquatting Attack Discovered! 🚨
A malicious npm package impersonating TensorFlow.js has been identified, delivering heavily obfuscated malware that executes during installation. This threat poses serious risks to AI/ML developers.
Key Highlights:
- Malicious Package: [email protected]
- Publisher: graphite7199, suspicious account.
- Attack Vector: Automatic execution via npm post-install scripts.
- Target: Windows systems.
Obfuscation Techniques Include:
- Hex string encoding
- Function name mangling
- Character code substitution
Protective Measures:
- Utilize tools like SafeDep’s vet and pmg to flag suspicious packages during installation.
- Ensure secure coding practices to defend against supply chain attacks.
Stay vigilant and take proactive steps to secure your development environment. For an in-depth technical analysis and continuous updates, visit our blog!
👉 Share this post and spread the word! Your awareness can help protect others in our community.